PSI-Mitarbeiter mit einem Account können das System standardmässig nutzen. Nicht-PSI-Mitarbeiter müssen über ihre verantwortliche Kontaktperson einen Account für externe Benutzer beantragen.
Das System steht ausschliesslich als Tunneling-/Proxy-System zur Verfügung. Dies bedeutet, dass nach dem erfolgreichen Login in das System KEINE aktive, nutzbare Shell zur Verfügung steht, die für eine weitere Verbindung ins PSI Lan genutzt werden kann.
Zu Beginn der Nutzung muss eine "Setup-Verbindung" zu hopx.psi.ch aufgebaut werden. Diese Verbindung richtet auf hopx.psi.ch den Zugang für den Benutzer ein. Sie muss interaktiv sein und offen gehalten werden. Ohne diese "Setup-Verbindung" sind keinerlei Verbindungen über hopx.psi.ch ins PSI-Lan möglich!
- Pro Benutzer ist nur eine aktive "Setup-Verbindung" zu
hopx.psi.chmöglich. (weitere Infos dazu sind unten zu finden) - die "Setup-Verbindung" kann mit einer oder mehreren Port-Weiterleitungen kombiniert werden (siehe unten)
- SSH-Clients (Putty, OpenSSH etc.) können so konfiguriert werden, dass SSH-Verbindungen ins PSI-Lan über die "Setup-Verbindung" erfolgen. (Stichwort: SSH-Multiplexing, ProxyJump, Connection Sharing)
Hinweis zu OpenSSH:
Das Kommando
ssh -J <user>@hopx.psi.ch <user>@beispiel-ssh-srv.psi.ch
funktioniert ohne vorherige "Setup-Verbindung" nicht, auch wenn das für gewöhnlich mit OpenSSH möglich ist!!!
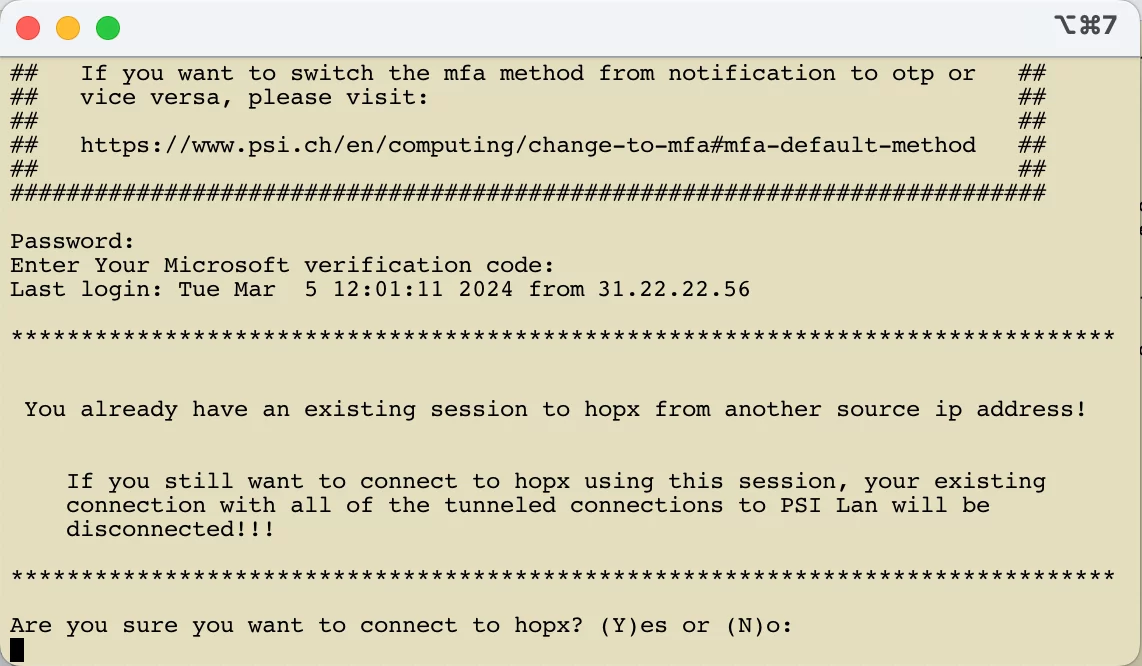
Die nachfolgende Abbildung zeigt die Ausgabe nach dem erfolgreichen Login.
Die Ausgabe nach dem Login enthält die folgenden wichtigen Informationen:
- Die IP-Adresse des Clients mit der die Verbindung zu
hopx.psi.chaufgebaut wurde. - Der Benutzername, mit der die Verbindung aufgebaut wurde.
- Die NAT-IP-Adresse, mit der die vom Benutzer durch
hopx.psi.chaufgebauten Verbindungen zu Systemen innerhalb des PSI-Netzwerkes erscheinen. - Das Datum und die Uhrzeit wann die Verbindung zu
hopx.psi.chgestartet wurde - Das Datum und die Uhrzeit bis wann die Verbindung zu
hopx.psi.chmaximal bestehen bleiben kann. Zu dieser Uhrzeit (nach Ablauf der maximalen Sessiondauer von 12h) wird die Verbindung zuhopx.psi.chautomatisch getrennt. Alle durch hopx.psi.ch aufgebauten Verbindungen ins PSI-Netzwerk werden ebenfalls unterbrochen.
Die Verbindung zu hopx.psi.ch kann mit "ctrl-c". beendet werden. Es stehen keine weiteren Kommandos zur Verfügung!
********* Achtung ****************
Wird die "Setup-Verbindung" zu hopx.psi.ch beendet, während die Verbindung(en) zu einem internen System noch aktiv/offen sind, dann werden diese ebenfalls beendet!!!
***********************************
Verhalten beim Aufbau von mehr als einer "Setup-Verbindung"
Erfolgt der Aufbau einer zweiten "Setup-Verbindung" zu hopx.psi.ch unter der Verwendung des gleichen Benutzernamens und der gleichen Source-IP-Adresse, dann wird diese Verbindung nach der erfolgreichen Authentisierung mit dem Hinweis auf die bereits bestehende Verbindung getrennt.
Erfolgt der Aufbau einer zweiten "Setup-Verbindung" zu hopx.psi.ch unter der Verwendung des gleichen Benutzernamens aber einer anderen Source-IP-Adresse als bei der bereits bestehenden Verbindung, dann wird der Benutzer nach der erfolgreichen Authentisierung vor die Wahl gestellt. Er kann die zweite Verbindung tatsächlich aufbauen, dann wird jedoch die erste Verbindung und alle dazugehörigen getunnelten Verbindungen ins PSI-Netzwerk getrennt. Oder er kann die zweite Verbindung beenden und mit der ersten weiterarbeiten. Die Antwort auf die Frage ist mit 'Y' , 'y' , 'N' oder 'n' zu beantworten.
Maximale Sessiondauer von 12 Stunden
Die Dauer des aktiven Zugangs ("Setup-Verbindung") zu hopx.psi.ch und allen dazugehörigen Verbindungen ins PSI-Lan wird analog zum VPN-Zugang auf maximal 12 Stunden beschränkt. Bis wann die Verbindung maximal bestehen bleiben kann, wird nach der erfolgreichen Authentisierung angezeigt (siehe oben). Im gleichen Fenster erfolgt fünf Minuten bevor die Verbindung getrennt wird ein Hinweis auf die bevorstehende Beendigung der Verbindung.
********* Achtung ****************
Wird die "Setup-Verbindung" zu hopx.psi.ch beendet, während die Verbindung(en) zu einem internen System noch aktiv/offen sind, dann werden diese ebenfalls beendet!!!
**********************************
Hinweis zu den möglichen Tunnel-Verbindungen
Bitte beachten Sie, dass nicht allen Benutzern des Systems die gleichen Möglichkeiten zur Verfügung stehen. Anhand der Art des Benutzeraccounts sind unterschiedliche Verbindungen über das System möglich.
PSI-Mitarbeiter
PSI-Mitarbeiter können über hopx.psi.ch die folgenden TCP-Verbindung ins PSI LAN tunneln:
| TCP Port Nummer | wird genutzt von |
|---|---|
| 22 | SSH |
| 80/443 | HTTP(S) |
| 445 | Windows File Server (z. B. fs00, fs01 or fs02) |
| >1023 | bspw. für RDP, VNC etc. |
Externe Benutzer
Externe Benutzer können über hopx.psi.ch die folgenden TCP-Verbindung ins PSI LAN tunneln:
- SSH-Verbindungen zu den Clustern
Merlin, RA, Login, MEGetc. - SSH-Verbindungen zu den Experiment-Sprungsystemen etc.
Diese SSH-Verbindungen sind nur möglich, wenn Sie über die entsprechenden Zugriffsrechte verfügen. Falls Sie über diese nicht verfügen, wenden Sie sich bitte an Ihre verantwortliche PSI-Kontaktperson.
Falls Sie weitere Verbindungsmöglichkeiten benötigen, müssen diese von Ihrer PSI-Kontaktperson für Sie beantragt werden.
Die bisher allgemein gültigen Zugriffsmöglichkeiten für externe Benutzer wie:
| TCP Port Nummer | wird genutzt von |
|---|---|
| 22 | SSH |
| 3389 | RDP |
| 5900 | VNC |
werden in den kommenden Wochen nach und nach deaktiviert.
Hinweis zur Verwendung von VS Code
Das Remote SSH Plugin von VS Code versucht durch die Standardeinstellungen mehrfach eine unterbrochene SSH-Verbindung wieder aufzubauen. War ein Benutzer mit mehreren Systemen von remote via SSH verbunden und die Verbindungen wurden unterbrochen, dann versucht VS Code jede Verbindung automatisch wieder herzustellen. Dieses Verhalten kann auf hopx.psi.ch zu vielen fehlgeschlagenen Loginversuchen und im Extremfall zu einer automatisierten Blockade des Benutzeraccounts oder der Client-IP-Adresse führen.
Um dies zu verhindern muss man die Anzahl der automatisieren Verbindungsversuche im VS Code deutlich reduzieren.
Hierfür muss “Max Reconnection Attempts” auf 0 gesetzt werden: